At cVation, we have long been leveraging “Infrastructure as Code” (IaC) to provision resources to Azure. In fact, that is the only way we spin up Azure resources. However, it is not unheard of that someone has done what can be classified as “Portal Driven Development”, meaning one or more Azure resources have been created using the Azure Portal.
Infrastructure As Code (IaC)
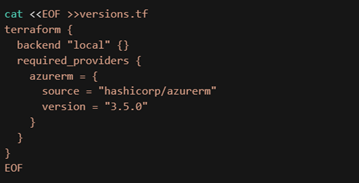
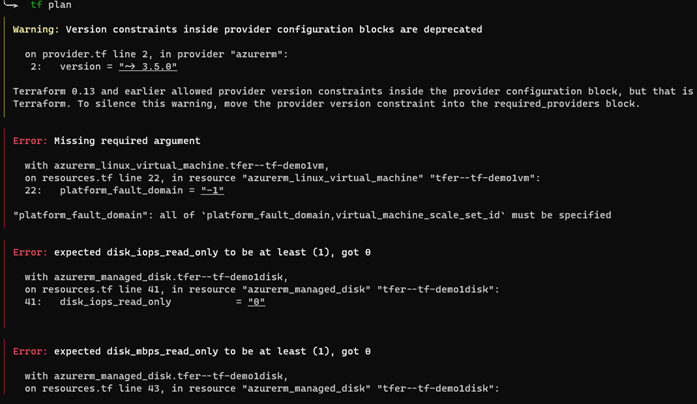
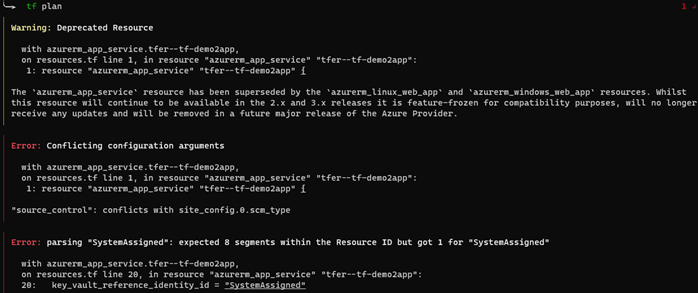
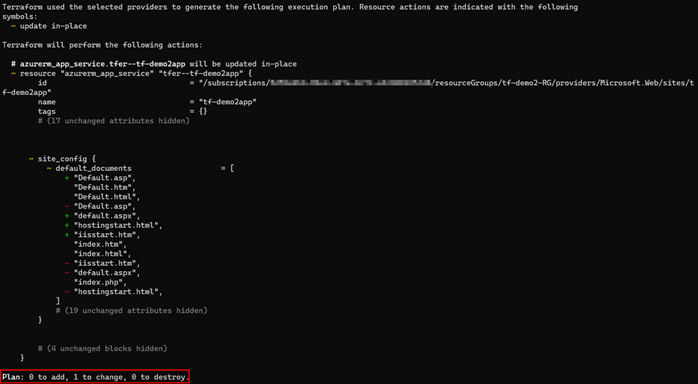
There are multiple tools available when deciding to leverage IaC. One of the most popular tools is “Terraform” developed and maintained by HashiCorp. Since Terraform has matured over the years, many third-party developers have extended the capabilities of what can be done natively using Terraform. In this blog post, we are testing two tools that provide extra capabilities, namely “Azure Terrafy” and “Terraformer”.
The goal of both tools is simple: Convert existing infrastructure to Terraform code.
The setup in Azure
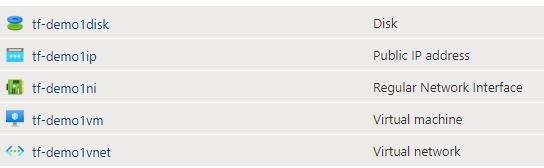
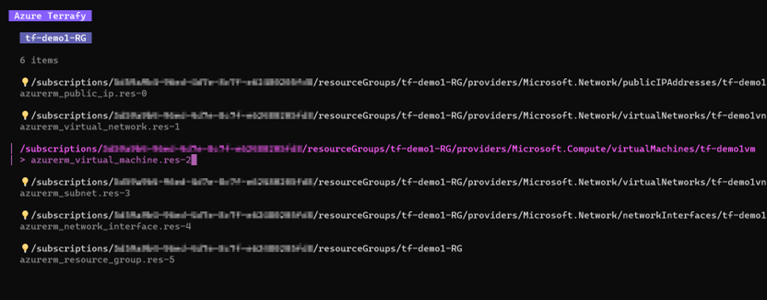
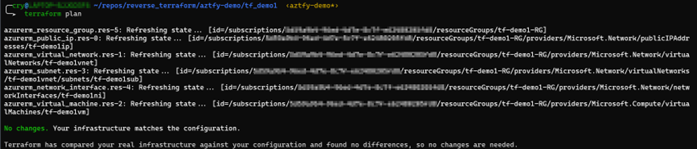
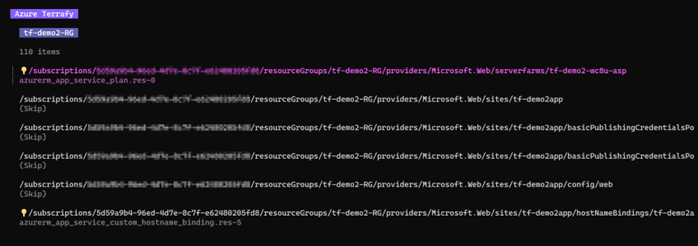
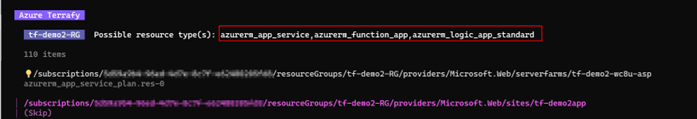
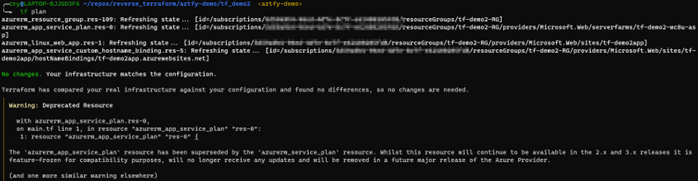
For the tests I have set up two resource groups containing a few resources. Resource group 1 contains the following: